A few months ago I came to the conclusion that our approach to security event monitoring was flawed. Traditional alert-based systems generate low fidelity indications of compromise and make a lot of work for SecOps triage teams. On the other hand, UEBA based systems fair no better. If their output…
Read More
Previously I introduced the idea of building your own UEBA system but I mainly talked about a specific data science project of mine designed to avoid the challenge of just adding risk scores to individuals or systems. In this article I want to take a step back and look at…
Read More
Self Organising Maps or SOM for short were originally invented by a Finnish professor, Teuvo Kohonen in the 1980s and therefore are sometimes called a Kohonen map. They are a form of neural network but are unusual in that they do not require labelled data to train (and are therefore…
Read More
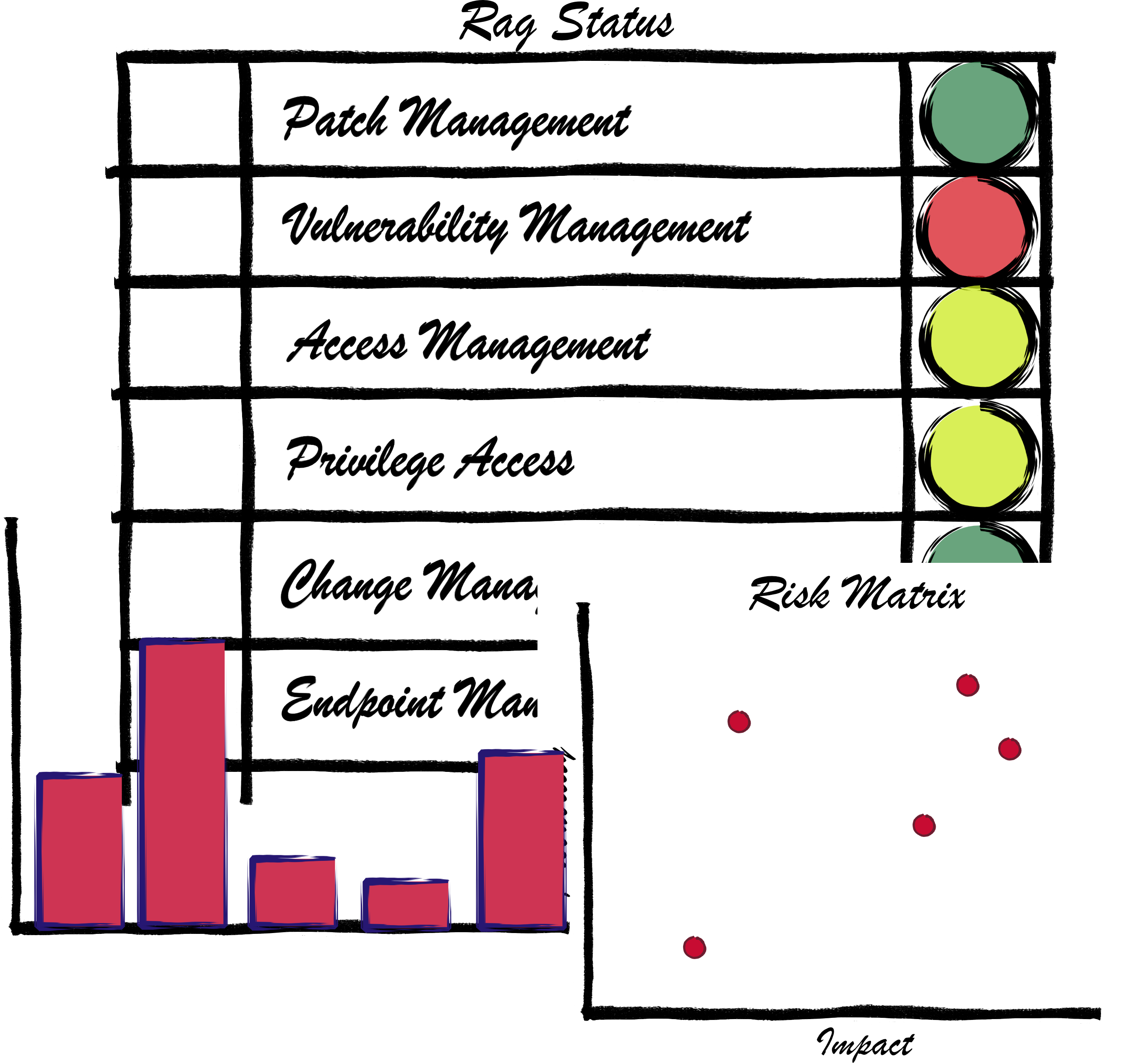
Security Information and Event Managment (SIEM) is a valuable tool to give you insight into what is happening, from a security perspective, in your environment. It allows you to react to developing threats and it gives you the ability to report upwards to management in a way they can understand.…
Read More
All Probabilities Are Conditional Even when statisticians tell you that the probability of some event is A what they are actually saying is that given all of the background the probability is A. Something as simple as rolling a six sided die gives you a 1/6th probability of any individual…
Read More
There seems to be a lot of confusion out there about how GDPR relates to security monitoring so I thought I’d take a moment to explain. GDPR is a wide ranging piece of legislation which was introduced to standardise data protection across EU states. In many ways GDPR was not…
Read More
In a previous post I talked about my project to use a Convolutional Neural Network (CNN) as a pre parser for security logs. I recently got a dump of anonymised data from a friend which arrived in directories identifying what it was and with two additional headers per file with…
Read More
I often find myself in minor disagreements with security practitioners who want to develop quantitative (as opposed to qualitative) risk frameworks for Information Security. I tend to stand my ground on this one if only because I too thought that way many years ago and have discovered the hard way…
Read More
I always have a few projects on the go but the main one I’m working on at the time of writing, concerns parsing of security logs. The start of any data pipeline for security monitoring starts with the ingestion of large amounts of log data. In order for this data…
Read More
So the cool kids keep talking about machine learning and how it is changing everything and you want to be part of that conversation? No problem, here is a roadmap to get you started… First of all, learn python programming. In my opinion everyone should know a little programming but…
Read More